A) controller IGMP snooping
B) multicast AP multicast mode
C) broadcast forwarding
D) unicast AP multicast mode
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
A) SOAP/XML
B) NMSP
C) CAPWAP
D) SNMP
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
A) Configure a second WLC to support half of the APs in the deployment.
B) Configure one single SSID and implement Cisco ISE for VLAN assignment according to different user roles.
C) Configure different AP groups to support different VLANs, so that all of the WLANs can be broadcast on both radios.
D) Configure 16 WLANs to be broadcast on the 2.4-GHz band and 16 WLANs to be broadcast on the 5.0-GHz band.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
For security purposes, an engineer enables CPU ACL and chooses an ACL on the Security > Access Control Lists > CPU Access Control Lists menu. Which kind of traffic does this change apply to, as soon as the change is made?
A) wireless traffic only
B) wired traffic only
C) VPN traffic
D) wireless and wired traffic
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A wireless engineer needs to implement client tracking. Which method does the angle of arrival use to determine the location of a wireless device?
A) received signal strength
B) triangulation
C) time distance of arrival
D) angle of incidence
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network engineer is experiencing issues enabling LAG on the WLC. Which four characteristics should be validated to ensure LAG configuration? (Choose four.)
A) ?ll ports participate in the LAG by default when LAG is enabled on the controller. y
B) Dynamic interfaces and management are moved to port 1
C) Primary and secondary ports are needed for each interface.
D) Multiple untagged interfaces to the same port are not allowed.
E) EtherChannel must be configured for mode "on" on the switch.
F) Only one functional physical port is needed to continue to pass traffic.
G) Multiple LAGs are permitted on the controller.
H) The WLC does not need to be rebooted to enable the LAG configuration.
J) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
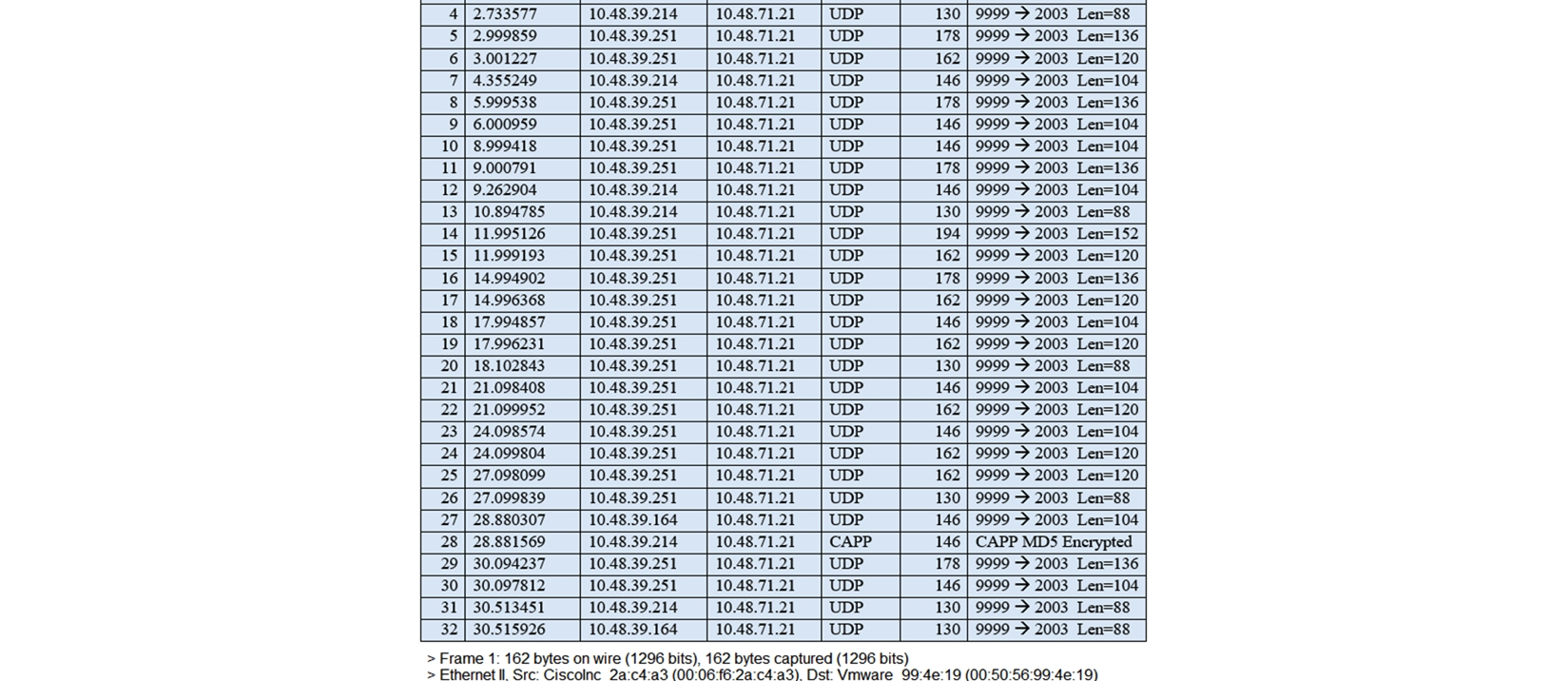 Refer to the exhibit. The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
Refer to the exhibit. The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
A) The Cisco CMX server receives NetFlow data from the WLC.
B) The Cisco CMX server receives NMSP traffic from the WLC.
C) The Cisco CMX server receives SNMP traffic from the WLC.
D) The Cisco CMX server receives Angle-of-Arrival data from the WLC.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is configured to use more than one port on the OEAP to extend the wired network?
A) remote LAN ACL
B) AAA override
C) client load balancing
D) remote LAN
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
A) permit-ACL
B) WMM required
C) mark
D) rate-limit
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network engineer is deploying 8865 IP phones with wireless clients connected to them. In order to apply the appropriate QoS, the IP voice traffic needs to be distinguished from client data traffic. Which switch configuration feature must be enabled?
A) Voice VLAN
B) QBSS
C) WME
D) QoS routing
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A corporation has recently implemented a BYOD policy at their HQ. Which two risks should the security director be concerned about? (Choose two.)
A) network analyzers
B) malware
C) lost and stolen devices
D) keyloggers
E) unauthorized users
G) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
CMX Facebook WiFi can allow access to the network before authentication. Which two of the following options are available? (Choose two)
A) Allow all the traffic before authentication and intercept HTTPs only.
B) Allow HTTP traffic only before authentication and block all the traffic.
C) Allow SNMP traffic only before authentication and block all the traffic.
D) Allow all the traffic before authentication and intercept HTTP only.
E) Allow HTTPs traffic only before authentication and block all other traffic.
G) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which list of characteristics must all controllers in a mobility group have in common based on best practices?
A) mobility group name, version of controller code, Control and Provisioning of Wireless Access Points mode, ACLs, and WLANs (SSIDs)
B) mobility domain name, version of controller code, and Control and Provisioning of Wireless Access Points mode
C) mobility domain name, version of controller code, Control and Provisioning of Wireless Access Points mode, ACLs, and WLANs (SSIDs)
D) mobility group name, version of controller code, and Control and Provisioning of Wireless Access Points mode
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network engineer has been hired to perform a new MSE implementation on an existing network. The MSE must be installed in a different network than the Cisco WLC. Which configuration allows the devices to communicate over NMSP?
A) Allow UDP/16113 port on the central switch.
B) Allow TCP/16113 port on the firewall.
C) Allow UDP/16666 port on the VPN router.
D) Allow TCP/16666 port on the router.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two steps are needed to complete integration of the MSE to Cisco Prime Infrastructure and be able to track the location of clients/rogues on maps? (Choose two.)
A) Synchronize access points with the MSE.
B) Add the MSE to Cisco Prime Infrastructure using the CLI credentials.
C) Add the MSE to Cisco Prime Infrastructure using the Cisco Prime Infrastructure communication credentials configured during set up.
D) Apply a valid license for Wireless Intrusion Prevention System.
E) Apply a valid license for location tracking.
G) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a WLAN for 50 branch offices that require central management. Which controller architecture do you use?
A) per-branch local controllers
B) anchor controllers
C) FlexConnect controllers
D) autonomous access points
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
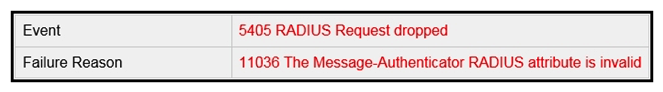 Refer to the exhibit. A wireless engineer has integrated the wireless network with a RADIUS server. Although the configuration on the RADIUS is correct, users are reporting that they are unable to connect. During troubleshooting, the engineer notices that the authentication requests are being dropped. Which action will resolve the issue?
Refer to the exhibit. A wireless engineer has integrated the wireless network with a RADIUS server. Although the configuration on the RADIUS is correct, users are reporting that they are unable to connect. During troubleshooting, the engineer notices that the authentication requests are being dropped. Which action will resolve the issue?
A) Allow connectivity from the wireless controller to the IP of the RADIUS server.
B) Provide a valid client username that has been configured on the RADIUS server.
C) Configure the shared-secret keys on the controller and the RADIUS server.
D) Authenticate the client using the same EAP type that has been set up on the RADIUS server.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Controllers WLC_1 and WLC_2 are in the same mobility group. A wireless client that does not have the same VLAN interface roams from WLC_1 to WLC_2. What happens to the client roaming?
A) The client context is deleted in controller WLC_1, and a new client context is created in WLC_2 to become the anchor controller.
B) The client context is moved from controller WLC_1 to controller WLC_2. The result is that the WLC_1 client context is deleted and WLC_2 becomes the anchor controller.
C) The client context is copied from controller WLC_1 to controller WLC_2. The result is that WLC_1 becomes the foreign controller and WLC_2 becomes the anchor controller.
D) The client context is copied from controller WLC_1 to controller WLC_2. The result is that WLC_1 becomes the anchor controller and WLC_2 becomes the foreign controller.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of information should be included in an installation report?
A) A complete characterization of the external WLAN environment.
B) The exact number of users the WLAN will support.
C) Soft copies of configuration for switches, routers, controllers, and location appliances.
D) A detailed description of the WLAN environment during the post-installation testing, for example, number of people present, furniture, no furniture, and sources of interference present.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer must implement Cisco Identity-Based Networking Services at a remote site using ISE to dynamically assign groups of users to specific IP subnets. If the subnet assigned to a client is available at the remote site, then traffic must be offloaded locally, and subnets are unavailable at the remote site must be tunneled back to the WLC. Which feature meets these requirements?
A) learn client IP address
B) FlexConnect local authentication
C) VLAN-based central switching
D) central DHCP processing
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 101
Related Exams